Server-supported tokens via user-credentials
If the end client has already implemented user login functionality into your backend servers, integrating a server-supported token is straightforward. This involves generating a unique ELSA token with a short expiration time to serve each end user only for the duration of their current login session. In the event of compromise, this token will only remain valid until its expiration time lapses. Think of this as a session token that grants the end user access to the ELSA API for a limited duration, after which a new ELSA token must be obtained.
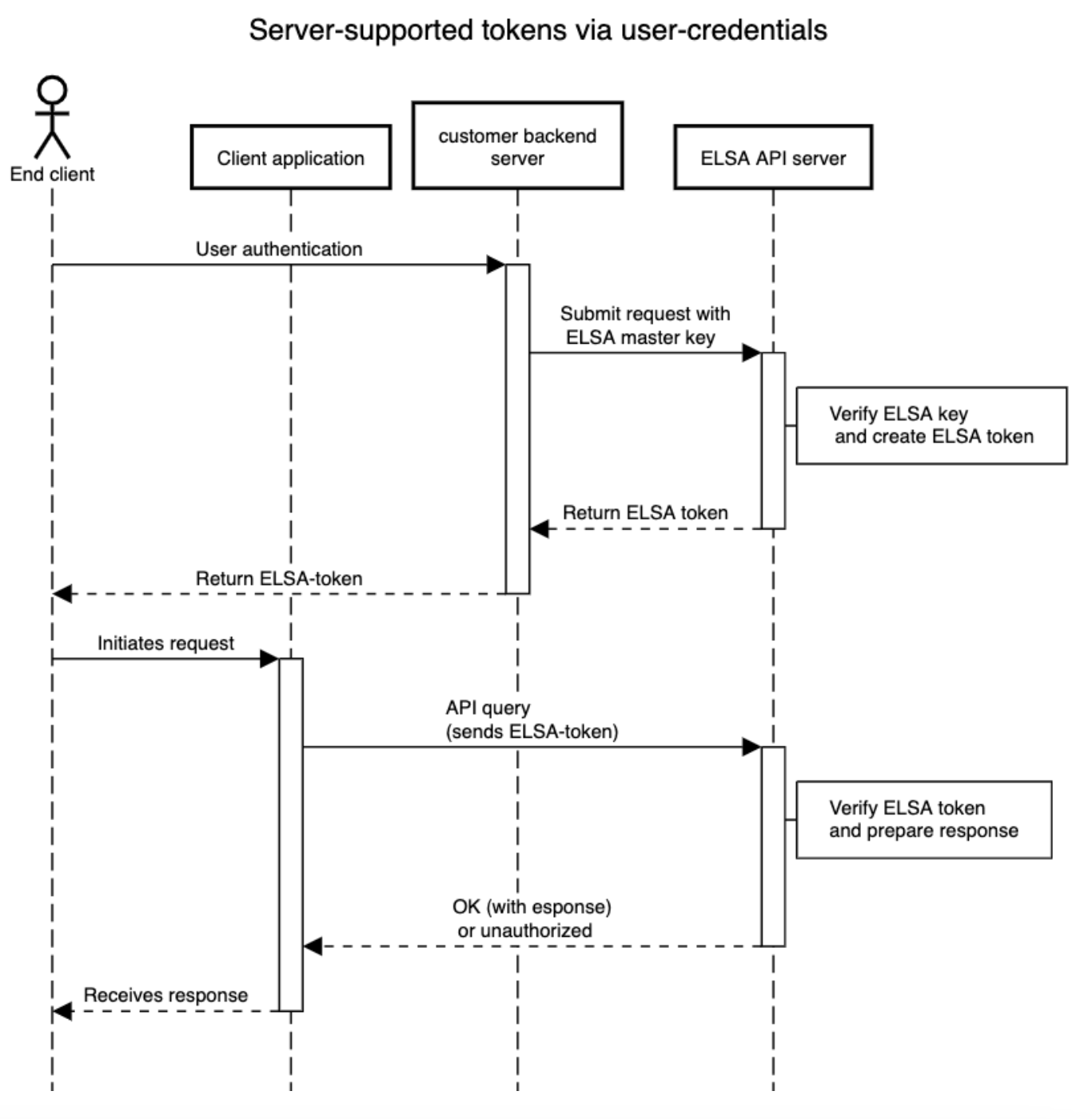
To implement this use-case, you will use the ELSA-Token API described below from your backend server. Then, you will provide the end-user app with a token to use in their calls. This approach is significantly more secure than deploying a non-expiring session token directly into the client app. This is similar to an OAuth2 implementation. For further details on this method, please refer to this article.