Stand-alone tokens
Stand-alone tokens are embedded within the client application and used in API calls to the ELSA servers. This option, considered the least secure among those outlined in this document, lacks customer control over potential misuse by end clients who may discover the token within the application. Although not recommended, it is often the simplest solution to implement on the client side. We recognize that in certain cases, such as when the client application does not require user authentication with the customer servers to utilize the API, this may be the only reasonable option.
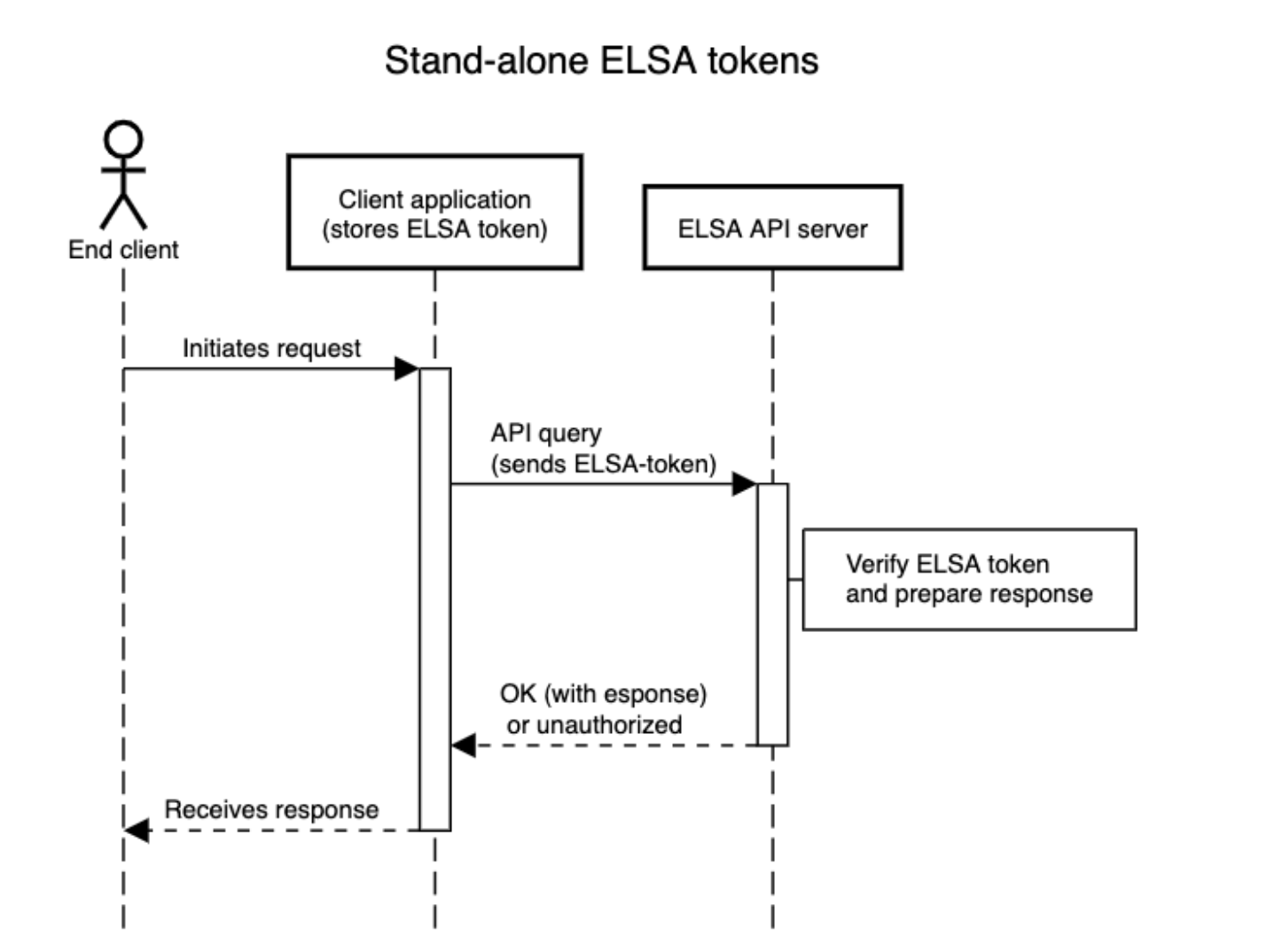
At ELSA, we take measures to safeguard your ELSA token from misuse:
- We implement reasonable rate limiting for calls originating from the same IP address.
- All communications occur exclusively through the HTTPS protocol.
To enhance security in your implementation, please consider the following:
- Whenever feasible, transmit the API_token as a header rather than a query parameter (both options are available in our API).
- Conceal the ELSA token within your application code to make it challenging for end users to locate and exploit.
- If your ELSA token has been compromised, promptly replace it in your app. You can do this either by utilizing the ELSA token API detailed below or by requesting a new token from us. Additionally, deactivate the old token as soon as possible. Currently, you can reach out to us to deactivate it on your behalf, although an API will soon be provided to automate this process.